So you want encryption on Windows. There's really 3 different layers of encryption you can do. Your first choice is to encrypt the files you want to protect manually by hand. This is extra EZ using something like 7zip. However it's super inconvenient. Everytime you want to access your protected files, you need to decrypt and unzip, then zip back up. Also, if you want to add anything to your secure archive, it's equally a pain in the ass.
Your next choice would be full disk encryption, which is a pretty good option. In this case, your filesystem is encrypted. This means that everything you drop on your disk is encrypted until you enter your password to mount the disk. This is the kind of thing you can get out of the box when you install linux usually. The downside to this is that everything in your partition is going to be encrypted, and there's some issues with portability. If I have a linux box and I want to dual boot, there's potential for fuckery when trying to mount your encrypted disk on windows, or vice versa because of windows' refusal to deal with other FS standards than FAT32 and NTFS. To be honest, the same could be said about Linux's refusal to add ZFS support (although that's changing! Ubuntu is putting its dick on the table and adding experimental ZFS support).
Then you can sit in the middle. In this case, you can add an abstraction layer on top of your filesystem, where files in a specific folder are encrypted. This is like what you get with eCryptFS or SecureFS. In this case, your files are portable and decoupled from the underlying filesystem. When you unlock your folder, it creates a mount running a virtual filesystem which provides the decrypted versions of the files. When you write, it automatically encrypts the files onto the original location on disk. The portability gains here should be obvious. In many cases, you can simply copy files and put them on a USB drive or email them individually.
In the case of SecureFS, there is a manifest file which sits alongside the encrypted folder. In my case, it's a JSON blob that looks like this:
{
"block_size" : 4096,
"encrypted_key" :
{
"IV" : "BLAH",
"MAC" : "BLAH",
"key" : "BLAH"
},
"iterations" : 65536,
"iv_size" : 12,
"pbkdf" : "scrypt",
"salt" : "BLAH",
"scrypt_p" : 0,
"scrypt_r" : 0,
"version" : 4
}
Without the manifest, the folder cannot be decrypted even with the password. You could store it separately and use it sort of like a 2FA. So SecureFS is great, but it's a command line tool. And who can be fucked to use CLI tools on windows? More seriously, there's a cross platform tool called SiriKali which can be used to mount these kinds of virtual filesystems, automatically unmount them, manage them, etc. It's a convenient little system tray tool. However, it doesn't come with any encryption tools like SecureFS. So it's easy, you just download a compatible binary like securefs and put it... uh...
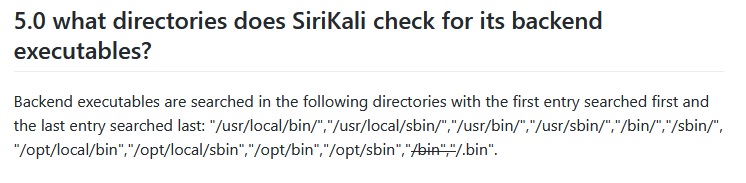
well fuck. As some of you smarty bois may have guessed, the place you should put these files on Windows is any folder that's in your path. In my case, I added it to my system path. Note that restarting SiriKali is not enough. You must reboot your computer. From there, we can go ahead and add a Favorite to create a quickly mountable bvolume that even has an idle timeout option. Although, I have no idea what units the timeout is in. Minutes? Hours? I assume minutes.
Once that's set up, you can install SiriKali just as easily on your linux partition, and easily share a securefs + NTFS volume between the two.
tl;dr
put the backend executables somewhere in your system path and reboot.
Stay comfy